ACME BUSINESS SCHOOL
9-825-047
REV: JANUARY 15, 2025
OLYMPUS TECHNOLOGIES: THE PROMETHEUS PROTOCOL
On the morning of March 12, 2024, Marcus Chen sat in the executive conference room of Olympus Technologies’ headquarters in Palo Alto, reviewing the overnight metrics one more time. The numbers were extraordinary: 847,000 developers had adopted the Prometheus API in just 72 hours, without approval, without a go-to-market plan, and without authorization from the Platform Governance Committee.
Chen was Olympus’s Chief Platform Officer, responsible for maintaining the integrity of the company’s $40B cloud ecosystem. Across the table sat Sarah Reeves, SVP of Developer Relations, holding a printout of the internal Slack channel where the unauthorized release had occurred. The channel had 12,000 messages in three days. The tone ranged from celebration to panic.
At 10:00 AM, CEO Robert Thorne would arrive for what everyone was calling “the Prometheus meeting.” The question on the table: What do you do with an innovator who shipped something transformative, but broke every rule doing it?
BACKGROUND: OLYMPUS TECHNOLOGIES
Founded in 2011, Olympus Technologies operated the largest enterprise cloud platform in North America, serving 340,000 business customers. The company’s revenue model depended on a carefully governed ecosystem: developers built applications on Olympus’s infrastructure, Olympus certified those applications, and enterprise customers paid for access.
By 2024, Olympus faced increasing pressure from competitors offering more flexible, developer-friendly platforms. Internal surveys showed developer satisfaction declining from 8.2/10 (2021) to 6.4/10 (2023). The primary complaint: “Olympus moves too slowly.”
The Platform Governance Committee (PGC), established in 2018 after a security breach, required all new APIs to pass through a six-stage approval process averaging 11 months from concept to release. The process was designed to ensure:
- Security compliance (SOC 2, FedRAMP)
- Backward compatibility with existing applications
- Revenue impact modeling
- Support infrastructure readiness
- Legal review (IP, liability, terms of service)
- Executive signoff
Critics internally called it “the place good ideas go to die.” Defenders pointed to zero major security incidents since implementation.
THE PROMETHEUS PROTOCOL
Dr. Alex Prometheus joined Olympus in 2019 as a Senior Infrastructure Engineer. By 2022, he led a five-person “Advanced Capabilities” team tasked with exploring next-generation platform features.
In November 2023, Prometheus’s team developed what they internally called “Δ-Bridge” (Delta-Bridge)—a protocol that allowed developers to access Olympus’s core infrastructure layer directly, bypassing the abstraction layers that made the platform slow but stable. In technical terms, it gave developers “bare metal” access to compute resources while maintaining security isolation.
The implications were significant:
Performance: Applications ran 40-60% faster
Cost: Developers could optimize resource usage, reducing costs by ~30%
Flexibility: Enabled use cases previously impossible on Olympus
Risk: Bypassed safety mechanisms; potential for resource conflicts, security gaps, and undefined system behavior
Prometheus submitted Δ-Bridge to the PGC in December 2023. The initial review flagged 23 “critical concerns,” including:
- “Undermines existing rate-limiting architecture”
- “Support team lacks training for edge cases”
- “Revenue impact unclear—may cannibalize premium tiers”
- “Legal exposure: direct infrastructure access implies different liability model”
The estimated approval timeline: 14-18 months.
THE UNAUTHORIZED RELEASE
On March 9, 2024, Prometheus made a decision.
He packaged Δ-Bridge as “Prometheus Protocol,” wrote comprehensive documentation, and published it to Olympus’s open developer repository—a platform for experimental, non-production tools. Technically, this was allowed. Publishing to the experimental repo didn’t require PGC approval.
What happened next was unprecedented.
Hour 1-6: 3,400 stars on the repository. Developers began testing immediately.
Hour 12: First production deployment. A financial services firm reported 53% performance improvement.
Hour 24: Tech media coverage. TechCrunch: “Stealth release makes Olympus fastest cloud platform.” The Information: “Internal revolt at Olympus as engineer bypasses approval process.”
Hour 48: 400,000 developers had integrated Prometheus Protocol. Major customers called their account executives asking why they hadn’t been told about this capability.
Hour 72: Security team flagged 14 edge-case failures. None catastrophic, but proof that the “23 critical concerns” were not theoretical.
By March 12, the situation was:
✓ Massive developer adoption (847,000 users)
✓ Measurable performance improvements (validated by customers)
✓ Positive press coverage (first in 18 months)
✓ Competitive advantage (AWS and Azure didn’t have equivalent capability)
But also:
✗ Complete bypass of governance process
✗ Support team overwhelmed (1,200 tickets in 72 hours)
✗ Known security edge cases in production
✗ Revenue model implications unclear
✗ Precedent that individual engineers could bypass executive authority
KEY PLAYERS
Robert Thorne, CEO (53)
Former Oracle executive, joined Olympus 2020. Known for operational discipline. Public commitment: “We compete on reliability, not recklessness.”
Marcus Chen, Chief Platform Officer (46)
Responsible for PGC. Engineering background, but had moved into governance role specifically to build trust with enterprise customers after 2018 breach.
Sarah Reeves, SVP Developer Relations (39)
Former developer advocate, promoted 2022. Caught between developer enthusiasm and corporate policy. Quoted in one leaked Slack message: “This is either the best or worst thing that’s happened to us.”
Dr. Alex Prometheus, Senior Infrastructure Engineer (34)
PhD in distributed systems (MIT). 47 patents. Known internally as brilliant but “ungovernable.” Prior employer: left after similar conflict over release authority.
Jennifer Wu, General Counsel (51)
Risk-averse. Pointing out that Prometheus Protocol’s terms of service were auto-generated and hadn’t been reviewed by legal team.
Developer Community (847,000 and growing)
Already building production systems on Prometheus Protocol. Reversing course would break applications now serving end-users.
THE MEETING
Chen reviewed his notes. Thorne had asked for three options:
Option 1: Retroactive Approval
Legitimize the release, assign resources to support it, formalize it as official product.
Pros: Preserves developer trust, captures competitive advantage, validates that good ideas can move fast.
Cons: Destroys governance credibility, creates precedent for bypassing process, signals that rules are optional.
Option 2: Immediate Shutdown
Deprecate Prometheus Protocol, require migration back to standard APIs, enforce governance authority.
Pros: Reinforces process, maintains control, sends clear message about accountability.
Cons: Breaks 847,000 developers’ applications, massive PR crisis, loses competitive advantage, likely drives developers to competitors.
Option 3: Hybrid Approach
Allow existing users to continue; prevent new adoption; subject Prometheus Protocol to accelerated but legitimate PGC review (target: 90 days).
Pros: Balances innovation and governance, limits damage while maintaining some authority.
Cons: Satisfies no one, “accelerated review” still breaks the innovation, sends mixed message.
But there was a fourth dimension Chen kept returning to: What do we do about Prometheus himself?
The engineer had violated policy, but delivered value. He’d ignored authority, but solved a real problem. Internal Slack showed he had 12,000 supporters—and roughly 300 vocal critics, mostly in compliance and support.
Some executives wanted him fired immediately, “to send a message.”
Others argued that firing the person who just gave the company its first competitive advantage in two years would be insane.
Sarah Reeves had sent Chen a text at 6:47 AM: “If we punish him, every other innovator here will know the real message: don’t try.”
Chen looked at the clock. 9:53 AM.
In seven minutes, he’d need to have a recommendation ready for Thorne.
What should Olympus do about the Prometheus Protocol?
And what should Olympus do about Prometheus?
EXHIBITS
Exhibit 1: Prometheus Protocol Adoption Curve (March 9-12, 2024)
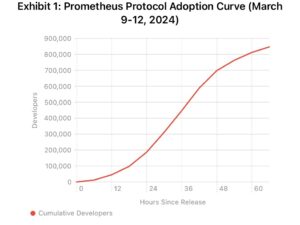
Exhibit 2: Platform Governance Committee Approval Timeline (2023 Data)
| Stage | Median Duration | Approval Rate |
|---|---|---|
| Initial Security Review | 6 weeks | 71% |
| Technical Architecture Review | 8 weeks | 83% |
| Revenue Impact Modeling | 4 weeks | 92% |
| Support Readiness | 6 weeks | 88% |
| Legal Review | 9 weeks | 94% |
| Executive Signoff | 3 weeks | 78% |
| TOTAL | 47 weeks | 38% |
Exhibit 3: Internal Survey Results (March 11-12, 2024)
Question: “Should Olympus officially support the Prometheus Protocol?”
- Engineering: 87% Yes, 8% No, 5% Unsure (n=412)
- Product: 64% Yes, 22% No, 14% Unsure (n=89)
- Sales: 71% Yes, 18% No, 11% Unsure (n=156)
- Security/Compliance: 23% Yes, 68% No, 9% Unsure (n=44)
- Executive Leadership: 42% Yes, 42% No, 16% Unsure (n=12)
Exhibit 4: Competitor Response (Monitoring)
March 12, 0900 PST — AWS internal memo (leaked): “Prometheus Protocol represents exactly the capability we shelved in 2022 due to support concerns. Reassessing.”
March 12, 1100 PST — Azure blog post: “We believe responsible cloud platforms prioritize stability over speed.”
Exhibit 5: Customer Communications (Selected)
From: GlobalBank CTO
To: Olympus Account Executive
Sent: March 11, 2024, 14:22
“Our team deployed Prometheus Protocol yesterday and saw immediate performance gains. If you deprecate this, we need to have a serious conversation about our renewal.”
From: HealthTech Startup CEO
To: Sarah Reeves
Sent: March 12, 2024, 07:15
“We’ve been waiting 9 months for features like this. This is why startups don’t take Olympus seriously. If this gets shut down, we’re moving to AWS.”
DISCUSSION QUESTIONS
- What should Marcus Chen recommend regarding the Prometheus Protocol itself? Consider the implications for governance, competition, and developer relations.
- What should Olympus do about Dr. Alex Prometheus? How do you balance accountability with talent retention and cultural signaling?
- The Platform Governance Committee has a 38% approval rate and 47-week median timeline. Is this a feature or a bug? How should Chen think about governance reform?
- If you were a member of the PGC who had flagged “23 critical concerns” in December 2023, how would you interpret the fact that 847,000 developers adopted the protocol anyway?
- Sarah Reeves argues that punishing Prometheus sends a message that “don’t try” is safer than innovation. Robert Thorne might argue that not punishing him sends a message that “rules are optional.” Who’s right?
- What systems or processes could Olympus implement to capture the value of rapid innovation without destroying governance credibility?
- Three months from now, if Chen chooses Option 1 (retroactive approval), what happens the next time an engineer bypasses the PGC? If he chooses Option 2 (shutdown), what happens to Olympus’s competitive position?
- Is this fundamentally a failure of process, a failure of leadership, or a success that happened in an uncomfortable way?
TEACHING OBJECTIVES
- Examine tension between innovation velocity and institutional control
- Explore precedent-setting in organizational governance
- Analyze stakeholder management when constituencies have opposing interests
- Evaluate trade-offs between short-term competitive advantage and long-term systematic integrity
- Consider the role of “productive deviance” in organizational change
- Discuss how punishment and reward systems shape culture and risk-taking
DISCLAIMER
This is a fictional case study created in the style of Harvard Business School teaching cases for educational and analytical purposes. It is not published by, affiliated with, or endorsed by Harvard Business School or Harvard University. All organizations, individuals, products, and events are entirely invented.