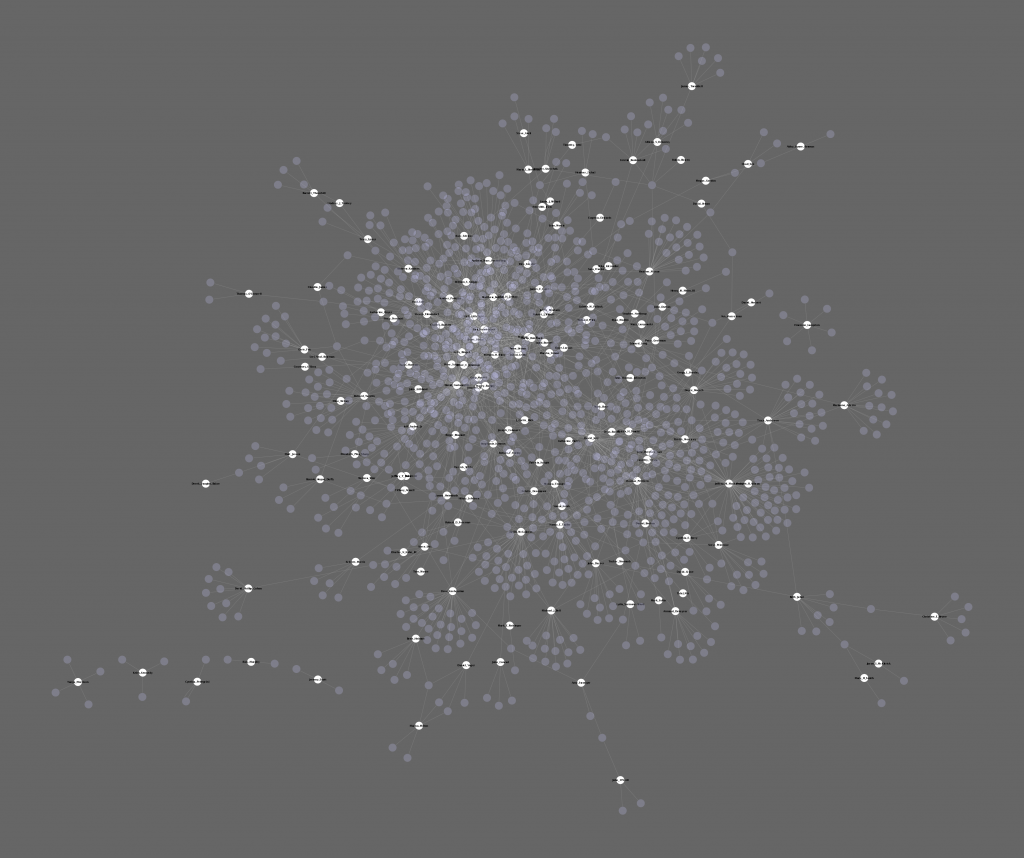
Thanks everyone for showing the strong interest in the Lobbyist map. I got a couple nice mentions at Mother Jones and LittleSis.org, but more importantly, I’ve added in all of the other names in the map.
Circles are people, squares are organizations, and white circles are the lobbyists in question.
If you’d rather the image than the flash bits, here you go, all 2.5MB of it.
A zoomable version of the earlier map is here:
[Thanks to Drew Conway for the Sea Dragon zoomable suggestion]
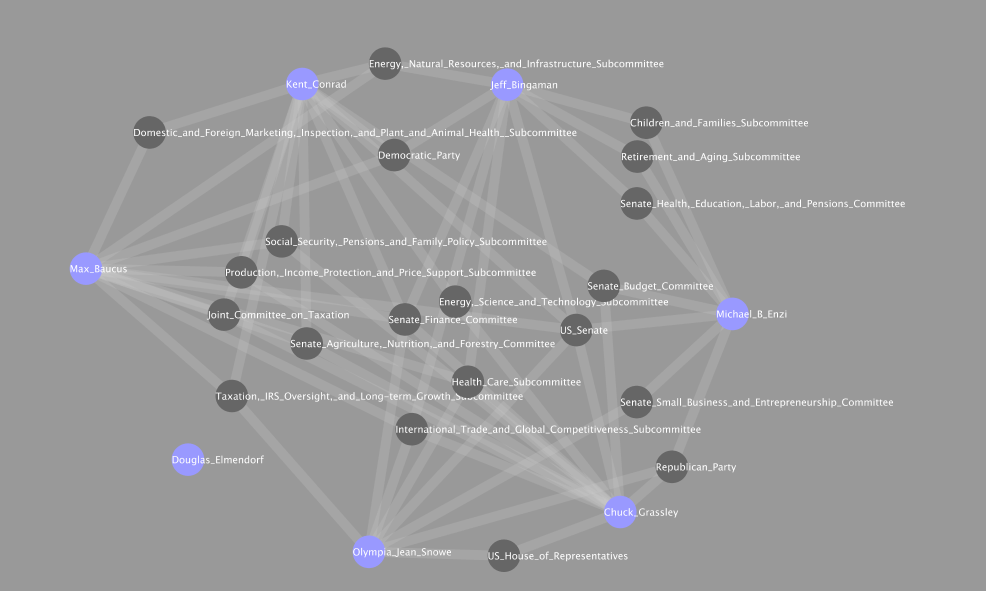
![The Negotiatiors [NY Times ]](http://graphics8.nytimes.com/images/2009/07/28/us/politics/28baucus.graphic.enlarge.jpg)
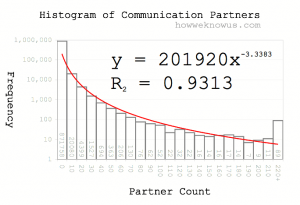
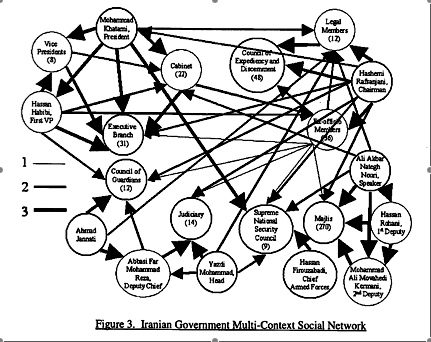
 Statistics::SocialNetworks has just been uploaded to
Statistics::SocialNetworks has just been uploaded to